PDF Structure Viewer
PDF security viewer affiche le fichier PDF et permet de récupérer les mots de passe.Liste des fonctions:
-Support de toutes les versions d’Adobe Acrobat y compris Acrobat 9
-Support de toutes les applications qui sauvegardent les fichiers PDF
-Support des fichiers dans n'importe quelle langue
-Suppression des mots de passe de l’utilisateur et du propriétaire (mots de passe “owner” et “user”)
-Suppression de la protection par le mot de passe
-Support du chiffrement RC4 à 40 et 128 bits et AES à 128 et 256 bits
-Support de l’attaque par dictionnaire et par force brute avec l’usage des patrons et des masques
-Trois version différentes
-Possibilité de supprimer la signature numérique
PDF security viewer supporte Windows, Linux et Mac. Cela vous permet de supprimer la protection quelque soit le système d'exploitation.
Attaque par masque
S’il y a l’information additionnelle à propos du mot de passe (la longueur du mot de passe en symboles ou n’importe quelle partie du mot de passe, information à propos de l’usage ou de l’absence de certains symboles et chiffres) la vitesse de la récupération peut être considérablement augmentée par la méthode de l’attaque par masque.
Attaque par dictionnaire
Selon la statistique le nombre important des mots de passe qui protègent les documents offices y compris les documents PDF contient un ou plusieurs mots du dictionnaire. La méthode d’attaque par dictionnaire permet de reduire le temps de récupération du mot de passe. PDF security viewer supporte l’attaque par dictionnaire en examinant des mots de passe qui comportent les mots ou leurs combinaisons possibles dans les différents registres et dans plusieurs langues. Les dictionnaires additionnels sont supportés.
Recherche par force brute
En cas d’absence d’information sur le mot de passe l’énumération de toutes les variantes possibles d’une certaine longueur est réalisée pour rétablir l’accès au document. PDF security viewer utilise les méthodes les plus récentes qui permettent d’atteindre la haute productivité de l’énumération.Acheter
- MyCommerce
- eSellerate
- SHARE-IT
- SWREG
- BMTMicro
- Rakuten Marketing
- NorthStar Solutions
- BlueSnap
- What is PDF Security Viewer
Estel PDF Security Viewer for Windows is a very useful application for searching passwords for password-protected Adobe Acrobat (PDF) documents.
A standard PDF document can have two passwords: "User" and "Owner". When "User" password (also known as Document Open password) is set, the password must be typed in to open the document. When "Owner" password (also known as Master or Permissions password) is set, one doesn’t need "User" password to open the document, but must type in "Owner" password to be able to open, copy, print, edit, and modify PDF files the way one needs. If a PDF file is secured with both types of passwords, it can be opened with either password, but only "Owner" password allows working with the document without any restrictions.
Now the process of recovering PDF files passwords becomes much easier with Estel PDF Security Viewer. The application allows searching for forgotten or lost "Owner" and "User" passwords using several deciphering algorithms.
Brute-force search involves selection of a possible password length and searching until the correct password is found. This strategy is effectively optimized for password recovery speed, thus short passwords can be recovered in just a few minutes.
Searching by template allows you to specify the template – already known symbols or characters – to decrease the total number of passwords to be verified.
Additionally, Recover PDF Password possesses exhaustive search option, which is recommended if a PDF file has both "User" and "Owner" passwords, and they are long and complex.
Besides brute-force search, you can also try dictionary search for password recovery, which tries every word or digit combination from special lists as a password.
Recover PDF Password also proposes file decryption. The decrypted file is saved without password and usage limitations. Moreover, your digital signatures can be removed from the decrypted PDF file.
Now encrypted PDF files will not bother you any more since you are using PDF Security Viewer. Our unique technology ensures the quickest recovery of the most complex passwords. As the result, you get the password for the protected PDF.
Features:
- Does NOT need Adobe Acrobat software
- Recovers "User" password, which is required to open the file
- Recovers "Owner" password, which permits to use PDF files without any restrictions (copy, print, edit, etc.)
- Brute-force and dictionary search are used to recover the password
- Network search uses CPU resources of computers on the network to make the speed of password search higher
- Patterns can be used to minimize search time if any part of the password is known
- Non-English characters in passwords are supported
- Automatically saves password search state and can resume after a pause
- Handy recovery history
- Decrypts PDF files
- Removes digital signature from a decrypted PDF file
- Supports PDF 1.7 (Acrobat 9.x) files, including 256-bit decryption
- Supports Windows XP, 2003, Vista, Windows Server 2008 x32, Windows 7, all 64-bit system platforms
- Supports multiprocessor systems for even higher speed of password search
Demo version limitations:
- A PDF file password can be recovered if it is not longer than four symbols when performing brute-force search or network search.
- When dictionary search is used, password of any length can be recovered, but only the first and the last symbols will be shown.
- Install PDF Security Viewer
PDF Security Viewer installation process is very easy. All you need to do is accomplish a few simple steps:
- Download the latest version of PDF Security Viewer at:
http://www.estelsoft.com/images/sv/estel_pdf_security_viewer.exe - Double-click it to start the installation process.
Follow the prompts given, study the License Agreement carefully, select the destination path and choose shortcuts you wish to be created.
- Finish the installation.
- Register PDF Security Viewer
Once you have purchased Estel PDF Security Viewer, the registration code will be e-mailed to you shortly. Delivery time may vary depending on your purchase options. The next step is to register your copy of PDF Security Viewer.
- Click "Help" –> "Enter registration info".
- In the new pop-up window enter Registration name and Registration code you have obtained from us:
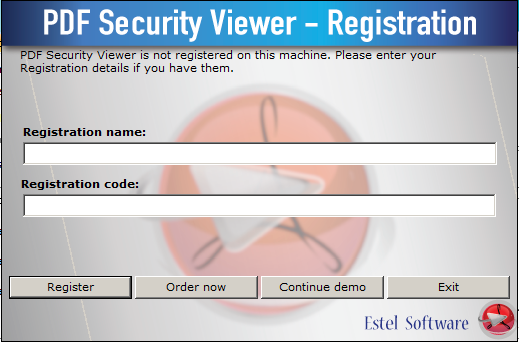
- Click "Register" button. That’s it!
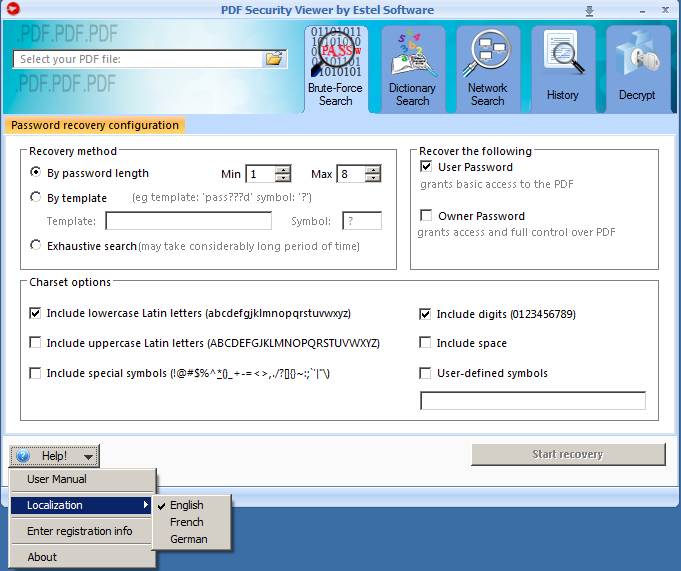
4. Brute-Force Search
After you launched PDF Security Viewer, you will see its main window:
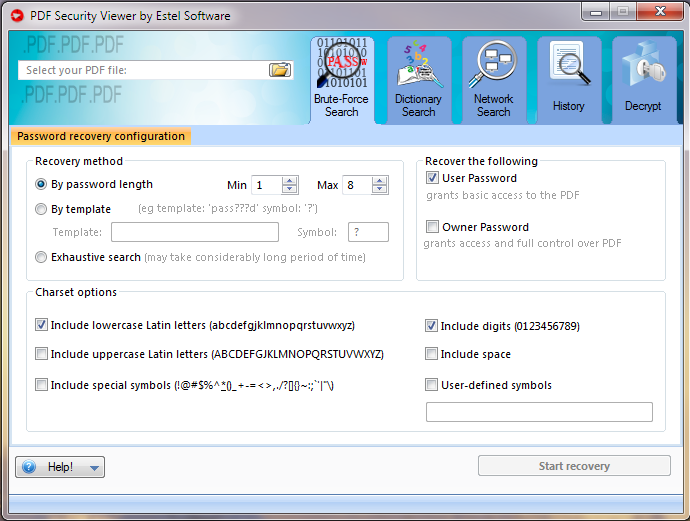
1. Select protected PDF file by clicking button and locating the file.
2. Now, choose the recovery method:
By password length – this is one of the most important options affecting checking time. Usually, you can test all short passwords in just a few minutes; but for longer passwords, you have to be patient and/or have some knowledge about the password (including the character set which has been used, or even better – the template).The minimum length cannot be set bigger than the maximum length, of course. If the minimum and maximum lengths are not the same, the program tries shorter passwords first.
By template – if you already know some symbols or characters in the password, you can specify the template to decrease the total number of passwords to be verified. For example, you know that the password contains 8 characters, starts with "x", and ends with "99". So, the template to be set is "x?????99".
Symbol - the symbol, used in template to substitute other symbols of search. For example, "?" is the symbol in "123??avc" template. Then only these symbols will be changed during password search, all other symbols will be left unchanged.
Exhaustive search – if the PDF file has both User and Owner passwords, and they are long and complex, you should try this feature. This option is recommended if your file uses 128-bit encryption. Recover PDF Password tries all possible encryption keys until finds the right one, and allows decrypting the file using that key – the resulting PDF file will have no security at all. That method gives 100% success but may take maximum time.
3. Both Owner and User passwords can be searched for.
4. Select various charset options:
Include lowercase Latin letters – all small Latin: abcdefghjiklmnopqrstuvwxyz
Include uppercase Latin letters – all Latin caps will be used: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Include special symbols - all special symbols (!@…): `~!@#$%^&*()-_=+\|,./<>?;:’"{}
Include digits – (0-9): 012345679
Include space – enables "space" character
User-defined symbols – enter symbols that are most likely to have been used in the password
5. When all the options are selected, all you have to do is click "Start recovery" button and wait.
During the decryption procedure you’ll be able to see overall decryption progress, elapsed and estimated time, etc.
Note that you can pause the recovering process at any time by clicking the corresponding button and continue it later.
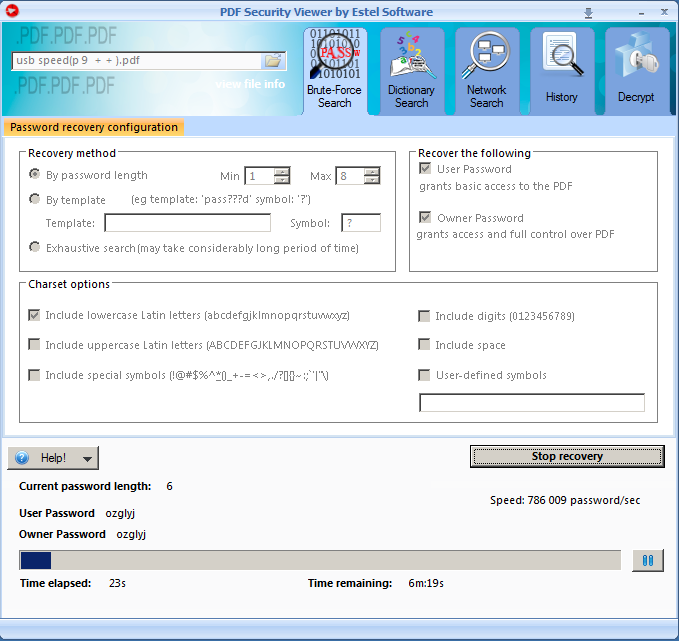
6. Now you can decrypt a file – save it without passwords and usage limitations. Refer to this section for details.
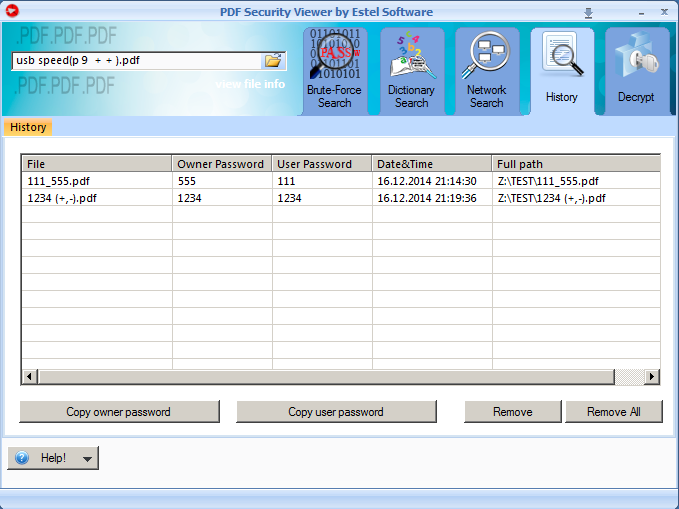
7. All the passwords are saved to History tab for your convenience.
5. Dictionary Search
Besides brute-force search, you can also try dictionary search for password recovery. This method uses special dictionaries (lists of words and digits). Every word or digit combination from these lists is tried as a password. These dictionaries are not just plain lists, because they contain such combinations as "qwerty" or "adminadmin", which are commonly used as passwords and which cannot be found in ordinary dictionaries.
Besides, you can significantly decrease the time of password recovery by applying Hybrid type of dictionary search. It checks not only all words/digits in the dictionary, but also their variations (e.g. the same word with different symbols appended to it).
Take these steps to start the password recovery using dictionary search:
- Select your PDF file: click button
 and locate the needed file.
and locate the needed file.
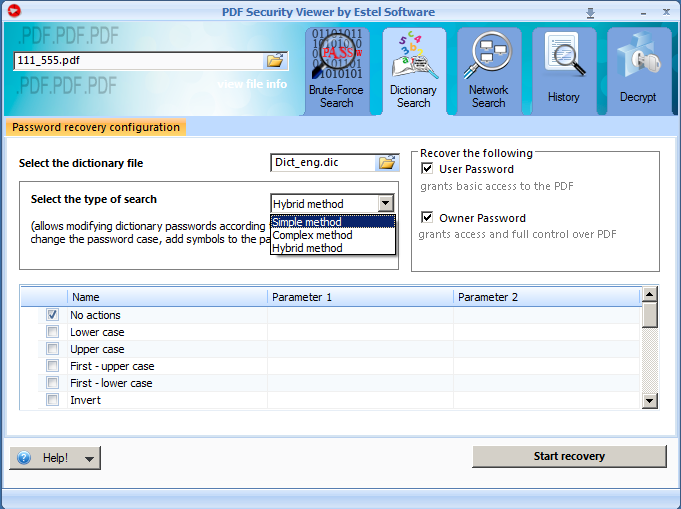
- Choose what type of password to recover: Owner, User or both.
- Select the dictionary file. Dictionary search uses special word lists for password recovery. You can use either default word lists, provided by Estel Software, or your own ones (either created by you or those, which are available over the Internet). Also, you can edit the default word lists. They can be located in the folder to which PDF Security Viewer is installed; usually it is C:\Program Files\Estel Software\PDF Security Viewer.
- Select the type of search. Three of them are available:
- Simple - Dictionary search tries every word/digit from the dictionary as a password.
- Complex – Dictionary search tries passwords composed of word pairs. This allows restoring complex passwords like "superadmin".
- Hybrid – Dictionary search checks all words/digits in the dictionary along with their variations. For example: words with different symbols appended to them.
Hybrid type of search requires that you set rules according to which search will be held. Each rule, chosen by you, will be separately applied to each word in the list.
To apply the rule, check the box next to it. Also, type the required parameters in the corresponding text fields, if needed (not all rules require parameters to be set). The full list of available rules is provided below.
Rules for Hybrid method are as follows:
|
# |
Rule |
Description |
|
1 |
No actions |
No actions will be applied to the initial word/digit. Dictionary search will check every word/digit from the dictionary without any modifications. |
|
2 |
Lower case |
Lower case will be applied to words. |
|
3 |
Upper case |
Upper case will be applied to words. |
|
4 |
First – upper case |
Only the first symbol will be capitalized; the rest will be lower-case. |
|
5 |
First – lower case |
Only the first symbol will be lower-case; the rest will be capitalized. |
|
6 |
Invert |
The case of each symbol in the word will be inverted: all upper-case characters will become lower-case, and vice versa. |
|
7 |
Invert half |
Only the first half of the word will be inverted. If the number of symbols in the word is uneven, the first half of the word (which is inverted) will be one symbol less than the second one. |
|
8 |
Reverse |
The word will be reversed: the order of symbols will be changed from the end to the beginning (e.g. Admin –> nimdA). |
|
9 |
Duplicate |
The word will be duplicated – repeated twice (e.g. admin –> adminadmin). |
|
10 |
Reflect |
The reversed form of the word will be added after the initial word (e.g. Admin –> AdminnimdA). |
|
11 |
Move left |
The word will be moved to the left relative to the first symbol, thus the first symbol will become the last (e.g. Admin –> dminA). |
|
12 |
Move right |
The word will be moved to the right relative to the first symbol, thus the last symbol will become the first (e.g. Admin –> nAdmi). |
|
13 |
Add to the beginning |
The symbol, typed in Parameter 1 text field, will be added to the beginning of the word. |
|
14 |
Add to the end |
The symbol, typed in Parameter 1 text field, will be added to the end of the word. |
|
15 |
Delete first |
The first symbol of the word will be omitted. |
|
16 |
Delete last |
The last symbol of the word will be omitted. |
|
17 |
Replace |
All symbols, indicated in Parameter 1 text field, will be replaced with symbols from Parameter 2 text field. |
|
18 |
Copy |
The word will be copied as many times as it is indicated in Parameter 1 text field. |
|
19 |
Copy first |
The first symbol of the word will be copied as many times as it is indicated in Parameter 1 text field. |
|
20
|
Copy last |
The last symbol of the word will be copied as many times as it is indicated in Parameter 1 text field. |
|
21 |
Copy all |
Each symbol of the word will be copied as many times as it is indicated in Parameter 1 text field. |
- When all the options are set, click "Start recovery" button and wait. During the password recovery procedure you’ll be able to see the overall progress, elapsed and remaining time, etc.
6. Network Search
To make the speed of password search even higher, PDF Security Viewer for Windows permits to use CPU resources of other computers, running Windows OS, which are available on your network.
A computer which central processing unit (CPU) is being used for password search is called "network agent". You can add any number of network agents and choose the number of CPUs to be used (by default, only one is used). In the future, you can remove the agent from the list, if needed.
PDF Security Viewer service is installed on network agents in two ways:
- either automatically, when installing the GUI version of PDF Security Viewer. This method is recommended as it does not require configuring your computer’s security settings.
- or manually, if you prefer to install the service remotely from the server machine (the administrator login and password are required). In this case only PDF Security Viewer service is present on the agent PC, but not the GUI version of PDF Security Viewer. PDF Security Viewer service is installed silently and does not require user interaction at the remote side.
The convenient chart in "Network Search" tab of PDF Security Viewer shows the agent’s hostname and IP address, the CPU used, the OS the agent is running and the password recovery progress.
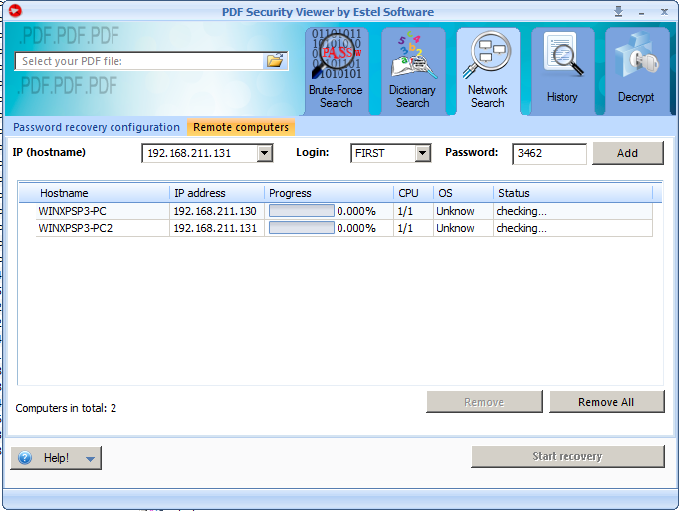
Each agent can have one of the following statuses:
- checking – the server is checking the agents’ statuses
- ready – PDF Security Viewer service is launched on the agent machine and is ready for password search
- searching for password – the agent is performing password search
- disabled - the agent is not being involved in the password search at the moment
- not installed – the agent machine is online, but PDF Security Viewer service is not installed there
- offline - the agent machine is offline
- not available - the agent machine is online, but access is denied for some reason (e.g., password was not entered)
- not responding – the agent is not responding. Make sure firewall is disabled on the agent machine.
To add an agent, do the following:
1. Add it by typing the agent’s hostname or IP address in the corresponding field or choose it from the drop-down list. Then press "Add" button.
2. If PDF Security Viewer service is not installed on the agent machine, enter the administrator login and password in the corresponding fields. The PDF Security Viewer service will be automatically installed there. PDF Security Viewer service is installed silently and does not require user interaction at the remote side.
Important notes:
- In case PDF Security Viewer service is already launched on the agent machine, make sure that firewall is disabled (or PDF Security Viewer is added to exclusions list) on the agent machine when adding this machine to the agents list on the server.
- When installing PDF Security Viewer service remotely, make sure that firewall is disabled (or PDF Security Viewer is added to exclusions list) on the agent machine. For Windows 7 and Vista User Account Control (UAC) should be disabled as well.
- Also, to allow remote connections, Simple file sharing should be off:
1. Go to Folder Options: untick "Use simple file sharing" option (for Windows XP) or "Use Sharing Wizard" option (for Windows 7).
2. For Server 2003 do the following:
gpedit.msc –> Computer Configuration –> Windows Settings –> Security Settings –> Local Policies –> Security Options –> Network Access. "Sharing and security model" should be set to "classic" type.
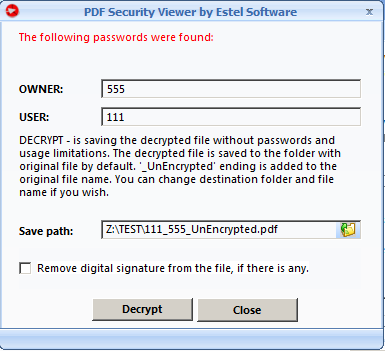
Decrypt PDF Files
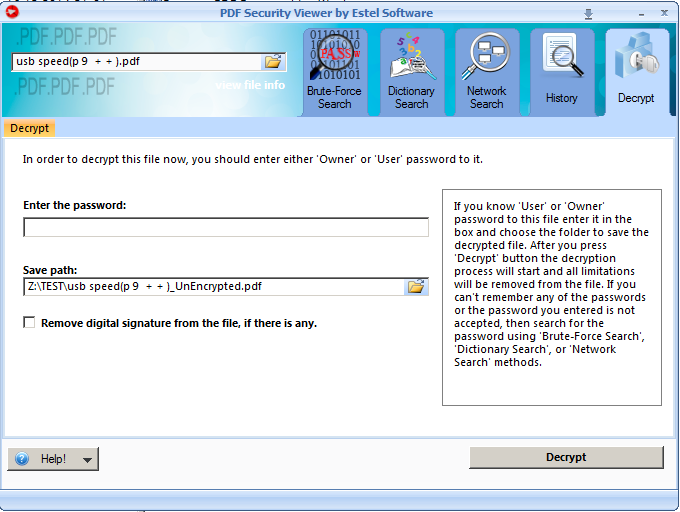
PDF Security Viewer proposes file decryption. The decrypted file is saved without password and usage limitations.
By default, the decrypted file is saved to the same folder with the original file.
"_UnEncrypted" ending is added to the decrypted file. You can change the file name and its destination path in the corresponding text field.
You can also check "Remove digital signature from the file, if there is any" box if you want to remove digital signature from a file. Digital signature is a method of an electronic document protection. PDF file will be analyzed, and a digital signature, if detected, will be deleted.
|
Notes: 2. PDF document can contain attachments of any file type. Currently, file attachments are saved during decryption for certain types of PDF files only. We are working on this issue in order to resolve it ASAP. This issue does not concern PDF Portfolio (multiple files of different formats assembled into an integrated PDF unit). PDF Portfolio is decrypted with all its component files. |
There are several possible scenarios of PDF file decryption:
- If you remember the PDF file password and want to save your doc without it, go to "Decrypt" tab:
Click "Decrypt File" button. Once decryption is over, you’ll see "The file is saved successfully" message.
|
Note: If the password you enter is not correct, PDF Security Viewer won’t be able to decrypt the file. You will receive this message:
Use Brute-force, Dictionary or Network search to recover PDF file password. |
- If you don’t remember the PDF file password, use Brute-force, Dictionary or Network search to recover PDF file password.
- If User password is absent, the file can be decrypted right away. In this case you’ll get a message as soon as you’ve selected the file:
Click "Decrypt" button. Once decryption is over, you’ll see "The file is saved successfully" message:
Note: If you still want to recover Owner password instead of decrypting the file right away, click "Close" button. Then check "Owner Password" box and click "Start recovery" button.
- File decryption is also available in "History tab", where you can view already recovered file passwords at any time and decide whether to decrypt the files.